Water and Wastewater Systems Are Especially Vulnerable to Cybercriminals
A Senate hearing about escalating cyberattacks against U.S. utility and water management agencies in July revealed some eye-popping statistics.
Testimony to the U.S. Senate Committee on Environment and Public Works included one alarming figure that nearly 45 percent of U.S. water and wastewater utilities allocate less than 1 percent of their budgets to the cybersecurity of their operational technologies.
Just last week, the FBI, Cybersecurity and Infrastructure Agency (CISA), Environmental Protection Agency (EPA) and National Security Agency (NSA) issued a joint advisory to spotlight ongoing malicious cyber activity targeting the information and operational technology networks, systems and devices of U.S. water and wastewater facilities.
There is a common belief that the next major catastrophe in the U.S. will originate from a cyberattack on a major system. Water undoubtedly is one of the most critical and vulnerable of those systems.
Attacks of this nature on U.S. companies and agencies may result in the shutdown of infrastructure critical to our daily existence. The Harvard Business Review reported earlier this year that ransom attacks increased by 150 percent in 2020 over the previous year, and that the amount paid by victims was up by more than 300 percent.
The City of Tulsa, Oklahoma, encountered a ransomware attack in May that prevented it from providing a wide range of services—such as utility bill pay, utility connection and acquiring police reports—to its citizens. The City reportedly had 4,500 computers connected to various online systems that were compromised.
Allen (Texas) Independent School District, which serves nearly 22,000 students, said it was victimized by a September ransomware attack that disrupted some systems. Hackers reportedly threatened to make public the personal information of staff members and students if the district didn’t pay.
Finally, one of the most publicized ransomware attacks of 2021 targeted Colonial Pipeline. The attack disrupted gasoline supplies all along the East Coast.
Key Definitions
“Malicious actors,” as they are called, are making headlines across the world, stealing critical information or demanding ransoms while vital systems are shut down.
Where are cybersecurity improvements being made to combat these attacks? Here are some key areas.
Incident response: As noted in the City of Tulsa attack, customers were affected in some fashion for weeks. Incident response teams react to and manage the attack immediately. They isolate affected systems, negotiate if necessary, limit the damage done and facilitate recovery such as validating what affected systems are no longer compromised.
Forensics: This process of collecting and analyzing data from an attack is instrumental in system vulnerability mitigation and fortification.
Penetration testing: Identifying a potential incident before it takes place is paramount. Penetration testing involves examining weak points for possible intrusion into a system or network. The results enable steps to be taken that will increase resiliency.
Compliance and audits: Entities within different industries who are recognized as authorities author standards and may conduct inquiries and administer audits to ensure proper security measures are in place. The National Institute of Standards and Technology (NIST) is one of the most influential organizations advancing risk management frameworks, which provide a set of rules or best practices to mitigate cyberattacks.
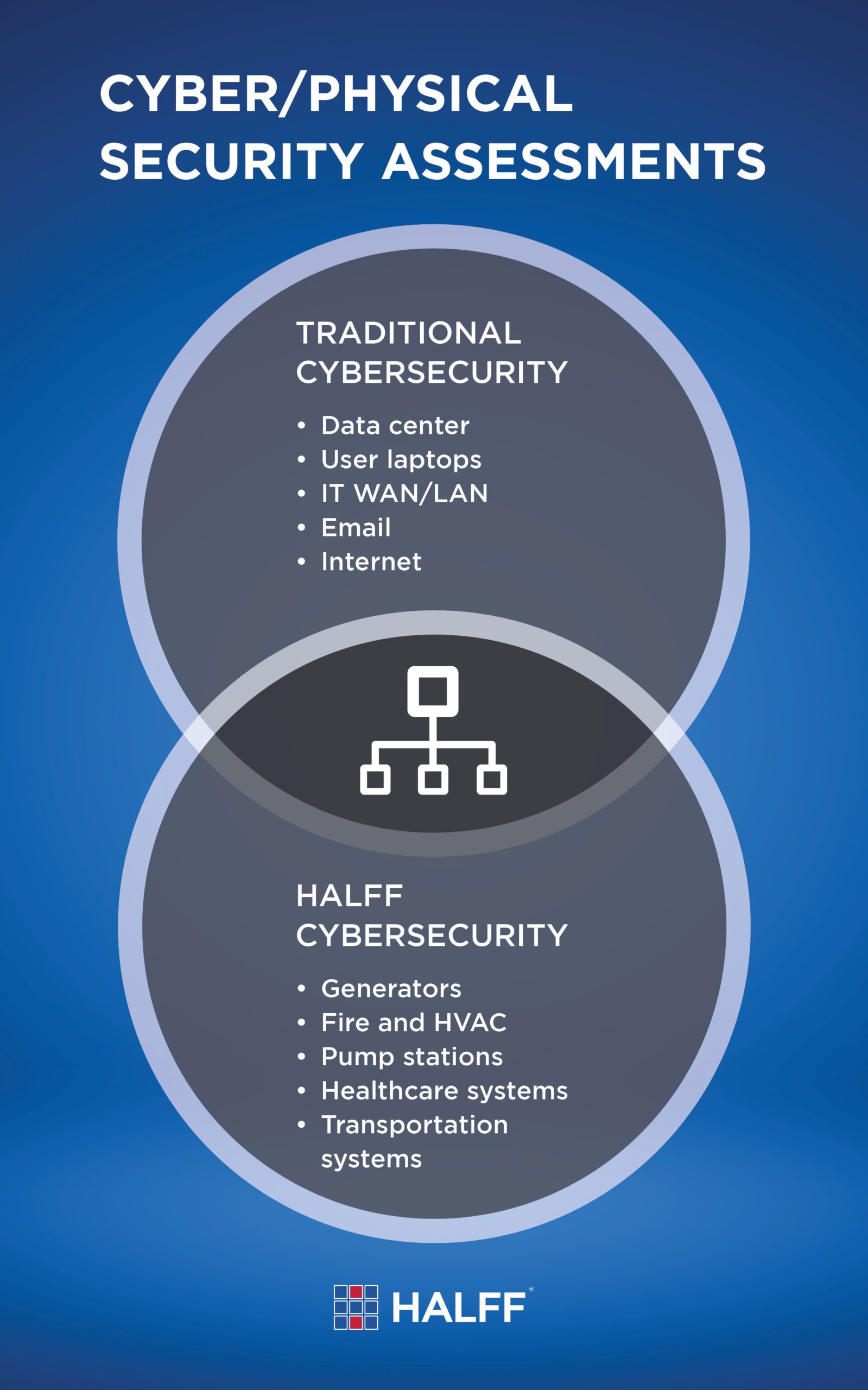
The Halff Approach
Halff is assisting Texas and Florida municipal clients and the U.S. Army Corps of Engineers in the areas of cyber and physical assessments as they pertain to operational technology. This includes systems, for example, located inside a building such as fire, HVAC and power generation connected to networks, plus SCADA systems that have a wide range of functions in drinking water treatment and distribution.
Assessments include a series of interviews to identify existing equipment and firewalls in place, training programs that are tied to the operation of key systems, their connectivity and more.
Strengths and weaknesses are identified through those assessments, which also probe information about equipment and devices outside of the internet—such as generators, actuators and pumps—which may be connected to other networks. The assessments pinpoint how updates are managed, how security patches are installed and how systems are monitored.
When considering water/wastewater operational technology, key questions might include the following:
-
-
Do you understand every water/wastewater component that is connected?
-
Do you keep a log showing that the latest firmware updates have been installed?
-
Are your camera systems connected to a remote location?
-
Are there any firewalls in place?
-
Do you maintain an inventory of every piece of equipment?
-
Who installs security patches, and is that information logged?
-
Vulnerable entry points can be identified once that information is known.
Halff is also designing solutions to meet the answers of those assessments. Moving forward, no two projects will likely be the same—even in the same sector. That’s because different projects typically have different missions. While one facility may require optimal connectivity for efficient operation, another requires minimal connectivity. Therefore, many of the “bells and whistles” are removed.
Agreeing on the level of remote monitoring and control that key operating systems require is an important step toward eliminating risk and improving resilience.
Halff offers a unique approach to help communities of all sizes implement their water utility risk and resilience assessments and emergency response plans—and develop operational improvements based on these assessments—to keep water and wastewater systems safe from a variety of threats.
For more information about operational technology assessments as they relate to cybersecurity, reach out to Director of MEP/ITS Engineering Jose Delgado at (956) 445–5222 or josedelgado@halff.com.